As Wisconsin voters start going to the polls in the 2020 election cycle, most counties in the state maintain websites that do not employ at least one of two basic practices that would help bolster their digital security and public confidence in their online platforms.
One is a relatively simple and widely available form of encryption security. Not using it creates a vulnerability that cybersecurity experts warn could open the door to malicious actors — something the state provides funding and technical support to fix.
News with a little more humanity
WPR’s “Wisconsin Today” newsletter keeps you connected to the state you love without feeling overwhelmed. No paywall. No agenda. No corporate filter.
Another is related to the name, or URL, of a web address. Most county election websites in Wisconsin do not use a URL ending in .gov. This practice is an uncomplicated way to ensure visitors of the validity of a government website, according to cybersecurity experts and the Wisconsin Elections Commission.
These practices potentially leave Wisconsin susceptible to election night chaos because the state, unlike others, relies entirely on counties to post unofficial election night results on their own websites. Bad actors could conceivably leverage these vulnerabilities for a number of ends, including rerouting visitors to false lookalike web pages that report inaccurate information.
While these practices do not necessarily pose a direct risk to the integrity of Wisconsin’s voting infrastructure or official election results, cybersecurity specialists contend they could damage public trust in the credibility of the state’s election administration and may point to more serious security lapses lurking behind the scenes.
WisContext reviewed HTTPS encryption security and the use of .gov domains by Wisconsin counties in March 2020 — the practices reported here are current as of March 10, 2020 and are likely to change. WisContext did not review the web practices of the 1,000-plus municipalities in the state that are responsible for administering elections but not for publicly reporting unofficial results.
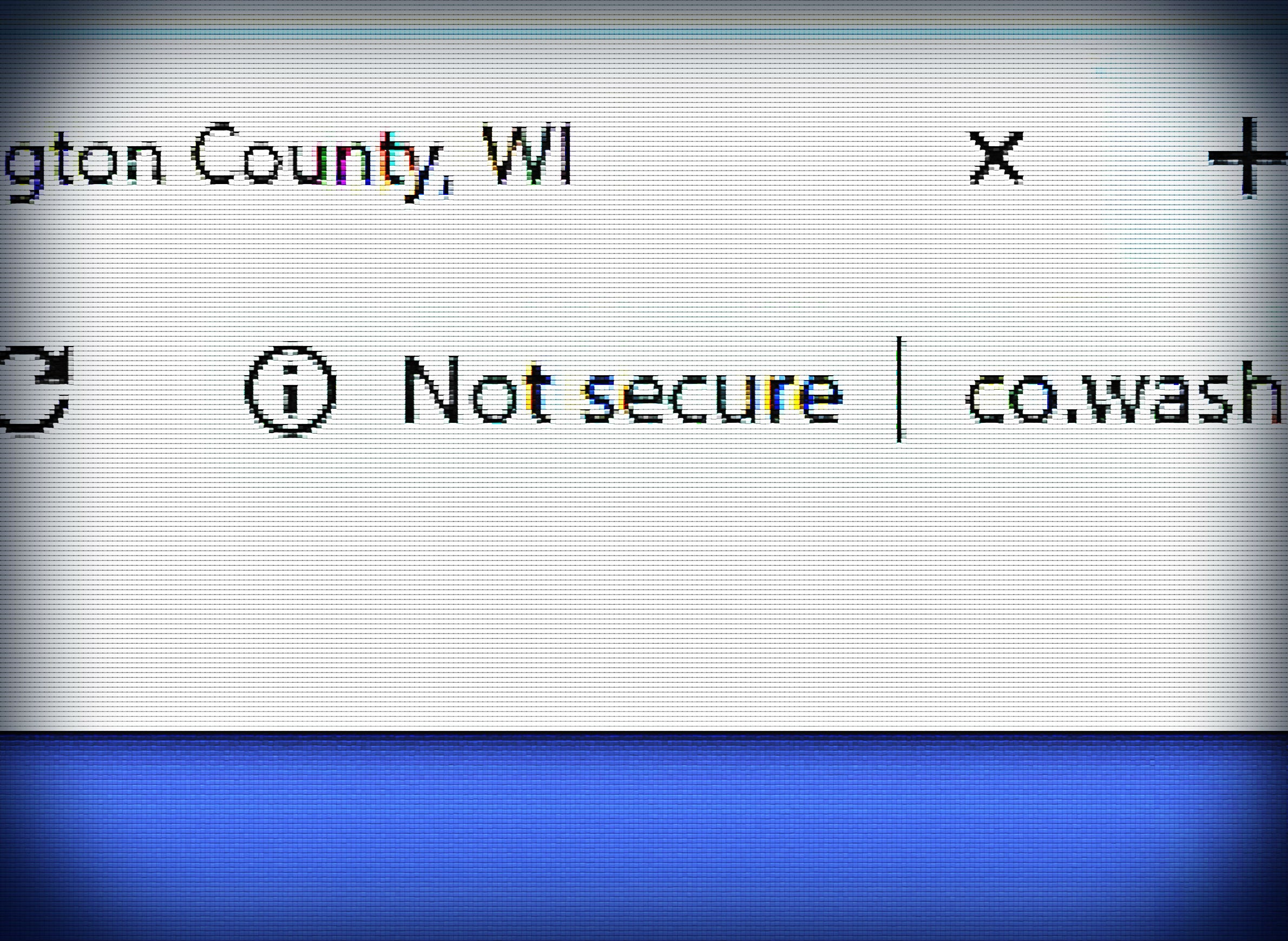
The encryption security 13 county websites lack is commonly known as HTTPS. It is easily identifiable to website visitors on major web browsing applications. On Google Chrome and Firefox, for instance, a website’s use of HTTPS is plainly visible via an icon of a locked padlock that appears on the left side of internet browsers’ web address bars. The icon assures visitors that their connection and communications with a website are encrypted and therefore safe from prying eyes and covert meddling. Websites without the security often feature language like “not secure” or an icon of an unlocked padlock or one with a red slash across it in the same left hand position of an address bar.
Meanwhile, use of a .gov domain is restricted, with the U.S. federal government controlling access to it. This setup means only legitimate units of government can have a website name ending in .gov. Counties must also gain approval from the federal government to use email addresses ending in .gov. Other domains, even ones that may seem more official, such as .org or .us, are easily accessible to anyone who can pay for them.
Fourteen of Wisconsin’s 72 counties use a .gov domain, and 59 counties employ HTTPS encryption security on their websites. Seven counties do not employ either practice: Kewaunee, Manitowoc, Marquette, Monroe, Rusk, Trempealeau and Washington.
Only eight counties in Wisconsin maintain an HTTPS-encrypted website with a domain ending in .gov.
Cybersecurity practices and priorities
Special Counsel Robert Mueller’s yearslong investigation into Russia’s interference in the United States’ 2016 elections concluded that an objective of that interference was to sow distrust in the nation’s democratic processes. U.S. intelligence agencies warned Congress the Russian government has similar goals in 2020.
The ongoing potential for interference is driving renewed attention to vulnerabilities in American election systems. Cybersecurity vendor McAfee published a report in February 2020 outlining how the use of .gov domains and email addresses and HTTPS encryption would help improve the security of local governments’ online elections infrastructure.
“McAfee’s assessment is well reasoned,” wrote Reid Magney, a public information officer for the Wisconsin Elections Commission, in an email to WisContext.
“In Wisconsin, we consider the use of encrypted (HTTPS) websites to be a higher priority than the use of .gov emails,” Magney added.
This prioritization is because the use of .gov domains is not necessarily more secure than using another domain. Its value lies more in cuing citizens to a government website’s legitimacy, Magney noted.
The Wisconsin Elections Commission provides technical assistance and grant funding to help communities make the switch to HTTPS encryption, Magney indicated, adding that it is working with the state Department of Administration “to develop .gov email solutions for county and municipal clerks.”
HTTPS encryption has been widely available for years and is considered a standard security practice in the business world, explained Walter Schilling, a professor in the software engineering program at the Milwaukee School of Engineering.
“The number of counties that are not using HTTPS is kind of scary,” Schilling said. He emphasized that a lack of the encryption security opens the door to so-called “man-in-the-middle” attacks.
A man-in-the-middle attack occurs when a malicious actor quietly hijacks an unencrypted connection between website visitors and the website’s server. Such an attack can take several forms, depending on the aims of the hacker. In the case of county elections websites in Wisconsin, this type of attack could include rerouting election-night visitors from legitimate websites that report unofficial results to dummy websites that appear virtually identical but provide false information.
“And you as a user would not really have any knowledge this is going on,” Schilling said.
However, Schilling noted that the ability to pull off an attack like this on a large scale would require a sophisticated operation.
“That’s an unlikely scenario,” he said. “The likelihood of a large-scale attack resulting in a tremendous amount of problems is probably not what I would be concerned with.”
Still, Schilling said the simple fact that more than a dozen Wisconsin counties continue to maintain public websites without the widely available encryption security poses troubling questions about their broader cybersecurity practices and priorities. For instance, if county employees are signing into the backend of websites via a similarly unencrypted connection, their login credentials could be stolen in targeted attacks.
There are many ways a website can be configured, though, and Schilling said just because a county’s public-facing site lacks HTTPS encryption does not necessarily mean other parts of the website hidden from public view also lack such security.
“It’s not unheard of that you log in through some additional portal,” Schilling said. However, if that portal also uses an unencrypted connection, “then we’ve got some potential danger to their credentials,” he added.
Website upgrades remain in the works
One of the websites lacking HTTPS encryption is operated by Door County. Some recent elections have been decided by narrow margins in the county: Of 17,608 votes cast for president in Door County in 2016, fewer than 600 votes separated Donald Trump and Hillary Clinton, the top two finishers.
In 2020, Door County officials are racing to complete work on a new, more secure website before the spring election on April 7. However, the process has been slower and more challenging than officials anticipated.
Door County Clerk Jill Lau is the official responsible for coordinating elections and reporting results in the county. Lau said the Wisconsin Elections Commission contacted her office in December 2019 with an offer for grant funding to add HTTPS encryption security, and she took the offer to the county’s IT department.
“I was told by the IT department that we didn’t need the money because our new website would have everything we needed,” Lau said.
“We are still in the process of updating our website,” she added, noting her frustration with the speed of that process.
“I was assured that it would be updated by January 1. It’s March 5 and we’re still not live. I’ve been informed that it will meet the [security] requirements we need. Do I know it will? No. It depends on who I talk to in the IT department. It’s an interesting world.”
Joanne Kurowski is the assistant IT director for Door County and is managing the rollout of a new website. Kurowski said she was hired in mid-2019 with the understanding that upgrading the county’s website was a top priority. However, she said she and others underestimated how much time would be required to build a new and more secure website to accommodate the county’s many digital goals and constituencies.
“The site delay was partially because of my handicap with my new job,” Kurowski said. “I’m not familiar enough with the organization to know how the data would flow, and it developed from a small to a very big project.”
Still, Door County is one of a handful in the state already using a .gov domain, and Kurowski is confident the new website with HTTPS encryption will be live before April.
“It’s almost finished,” she said. “If I have to stay here 24 hours a day, 7 days a week, it’ll be ready.”
Meanwhile, Washington County is the most populous county in Wisconsin that uses neither a .gov domain nor HTTPS encryption for its website. Officials there remain in the process of moving toward recommended web practices.
Ashley Reichert, the county clerk, said the county has a plan to roll out upgrades in stages. First, its IT department will transition the current site to a .gov domain and add HTTPS security, she said. That will later be followed by a whole new website, also with HTTPS encryption and at the same .gov domain.
Reichert said the first stage should occur “within the next few weeks” with the new website following sometime after the April primary but before the fall general elections.
“I was heavily involved in securing a vendor for our new website design and build, making sure that the election security, or the security component of the website in general, was extremely high,” Reichert said.
She added that the county board of supervisors is considering whether to add a devoted cybersecurity position to the county’s payroll this spring.
As counties work toward updating their cybersecurity practices, the widely variable status of local elections websites — in Wisconsin and elsewhere — remains a point of concern for David Levine.
Levine is an elections integrity fellow at the Alliance for Security Democracy, an international, nonpartisan initiative to secure democratic institutions against attacks from authoritarian governments. In February 2020, the organization published a guide Levine wrote outlining steps local elections officials can take to bolster election security. One of those steps is to beef up the security of their websites, including the implementation of HTTPS encryption.
Levine has administered elections as a local official in Idaho and Virginia, and he underscored the potential risks local governments open themselves up to by operating websites without HTTPS security. These risks multiply in states like Wisconsin, where the margin of victory in many statewide elections in recent years has been razor thin.
“Folks who don’t have HTTPS should be taking action to get an encrypted website,” he said.
Levine also recommended that local governments move over to .gov domains.
“We need folks being able to trust the information on the local website,” he said.
One Wisconsin county that went live in March 2020 with a new website that includes encryption security for the first time is La Crosse. County clerk Ginny Dankmeyer said the new site would help ensure the integrity of unofficial results reported on election night.
“As much as we put out there that these election results are unofficial on election night, no one seems to take that into consideration,” Dankmeyer said.
“Even though it’s unofficial, we want to try to be as accurate as we can,” she added. “If something happened in the background that’s going to be able to go in and change those results and cause chaos for us, we certainly don’t want that.”
Still, La Crosse County’s new website features a .org domain, and its previous website remained live and appeared alongside its new website in search engine results, a situation that could itself sow confusion even without the interference of bad actors.
This report was produced in a partnership between Wisconsin Public Radio, PBS Wisconsin and the University of Wisconsin Cooperative Extension. @ Copyright 2025, Board of Regents of the University of Wisconsin System and Wisconsin Educational Communications Board.